WIRELESSHART SECURITY
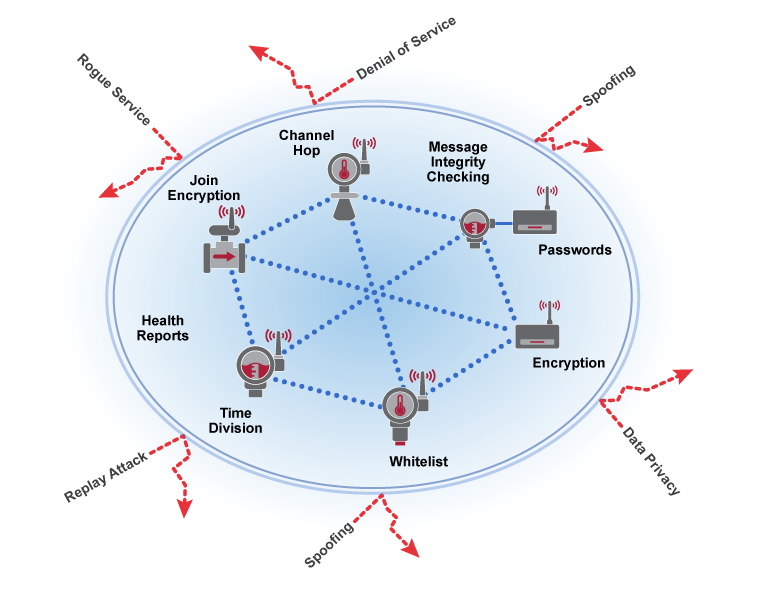
WirelessHART employs robust security measures to protect the network and secure data at all times. These measures include the latest security techniques to provide the highest levels of protection available.
AUTOMATICALLY PROTECTS VALUABLE INFORMATION
- Robust, multi-tiered, always-on security
- Industry standard 128-bit AES encryption
- Unique encryption key for each message
- Data integrity and device authentication
- Rotate encryption keys used to join the network – automatic or on-demand
PROTECTS WIRELESS NETWORK
- Channel hopping for security protection and co-existence
- Multiple levels of security keys for access
- Indication of failed access attempts, perhaps by a rogue device
- Reports message integrity and authentication failures
- Safe from Wi-Fi type internet attacks
Security is built in and cannot be disabled. Security is implemented with end-to-end sessions utilizing industry standard AES-128-bit encryption – approved by the National Security Agency (NSA) for top secret information. These sessions ensure that messages are enciphered such that only the final destination can decipher and use the payload created by a source device.
RISK ASSESSMENT / REDUCTION
To be a credible threat, an attacker must possess access, knowledge, and motivation. The WirelessHART technology Security architecture helps users address all three of these areas:
- Minimize, control and audit access
- Require high level of technical expertise to subvert
- Reduce the span and duration of any individual security breach
Wireless Sensor Network Security can be broken down into two main categories:
- Data security or confidentiality deals with maintaining the privacy and integrity of the information being passed over the network.
- Network security or availability deals with maintaining the functionality of the network in the face of internal and/or external attacks (intentional or unintentional).
DATA SECURITY
Security features associated with privacy aim to prevent eavesdropping by unauthorized devices inside or outside the network. A WirelessHART sensor network provides end-to-end CCM mode 128-bit AES encryption at the network/transport layer for every message in the network. In addition to individual session keys, a common network key is shared among all devices on a network to facilitate broadcast activity as needed. Encryption keys can be rotated as dictated by plant security policy to provide an even higher level of protection.A separate 128-bit join encryption key is used to keep data private that is sent and received during the joining process.
-
The join key serves as authentication to the Security Manager that the device belongs to this network.
-
The join key is treated separately from the other keys to enhance Security.
-
Join keys can either be unique to each device, or be common to a given WirelessHART network based on the user security policies.
-
Join keys can be changed after the device joins the network to further increase security.
Data Security features associated with integrity ensures that data sent over the wireless sensor network has not been tampered with or falsified.
-
WirelessHART uses two Message Integrity Check (MIC) Fields that are added to each packet.
-
At the session layer, the receiving device uses the session MIC along with the protected data to confirm that the contents of the packet have not been altered.
-
At the link layer a seperate MIC protects network routing information to prevent attacks that attempt to change the packet’s network/transport layer information.
Data Integrity also involves verifying that the packet has come from the correct source. The network/transport layer message integrity check field, the information used to generate the check field, and the sender/receiver unique session key that codes and decodes the data are tools that can be used to verify the source.
NETWORK SECURITY
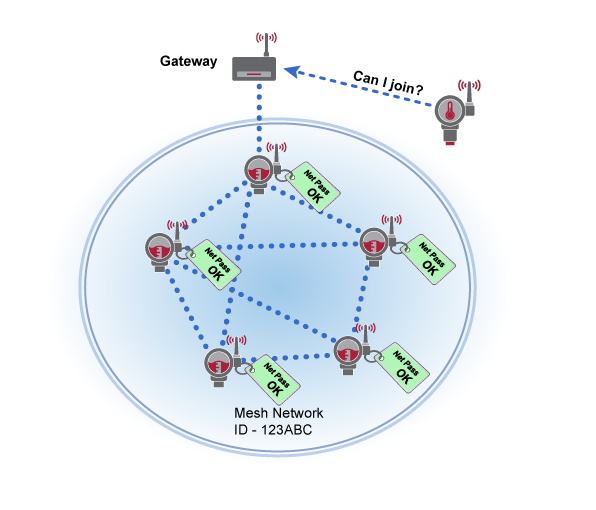
A wireless sensor network also needs tools to protect it against attacks. These attacks can attempt to compromise the network by inserting trojan horse devices, impersonating networks to get sensitive data from legitimate devices, and disrupting the network to deny service. Attacks can be launched from outside or inside the company by external people or employees. Successful network security depends upon techniques to support authentication, authorization and attack detection.
-
A WirelessHART Gateway and the wireless sensors joining the network must be configured to control which devices are allowed to access the network.
-
The network will only be secure if all the devices in the wireless network maintain security.
-
A WirelessHART Gateway has a secure authentication process which it uses to negotiate with all joining devices to ensure they are legitimate. As with all other network communications, all join negotiation traffic is encrypted end-to-end.
Denial of service attacks are aimed at impairing the proper operation of the system by interfering with communications within the wireless sensor network. These attacks may try to jam the radio or they may try to overload a process like packet acknowledgments.
-
WirelessHART devices report anomalous conditions that might signal a denial of service attack, such as traffic counters, retransmissions, etc.
-
WirelessHART devices can be network routers or just data sources – user configurable – but only authenticated messages are routed onward.
-
WirelessHART devices are not authorized to be network key servers or wireless network managers.

Join, network and session keys must be provided to the WirelessHART Network Manager…and join keys must be provided to Network Devices. These keys are used for device authentication and encryption of data in the network.
The WirelessHART Security Manager is responsible for the generation, storage, and management of these keys.
There is one Security Manager associated with each WirelessHART Network. The Security Manager may be a centralized function in some plant automation networks, servicing more than just one WirelessHART Network and in some cases other networks and applications.
Learn more about WirelessHART Security
Intrinsically Secure WirelessHART® Field Device Networks and the Industrial Internet of Things (IIoT) - Technical Paper